Issue: Facing synchronization challenges with Active Directory (AD) users in Microsoft Entra ID (formerly known as Azure AD)? You’re not alone. It’s a common scenario where AD users fail to properly sync with Entra ID, leading to the unintended creation of duplicate cloud objects, such as “[email protected]”. This guide addresses the synchronization pitfalls and offers effective strategies for seamless integration between your Active Directory and Microsoft Entra ID, ensuring a unified identity management solution.
Solution 01:
Step 1: Isolate the Problematic Object
Begin by relocating the user object encountering synchronization issues to an Organizational Unit (OU) that is not synchronized with Microsoft Entra ID.
Step 2: Trigger Manual Synchronization
Once the object is moved, manually initiate the Entra ID Connect synchronization process.
Start-ADSyncSyncCycle
Step 3: Cleanup Process
The duplicated user is now removed from Microsoft 365. Now connect to Microsoft 365 and check the Deleted Users
Connect-MsolService Get-msoluser -ReturnDeletedUsers
Permanent delete it from Microsoft 365
Remove-MsolUser -UserPrincipalName "[email protected]" -RemoveFromRecycle
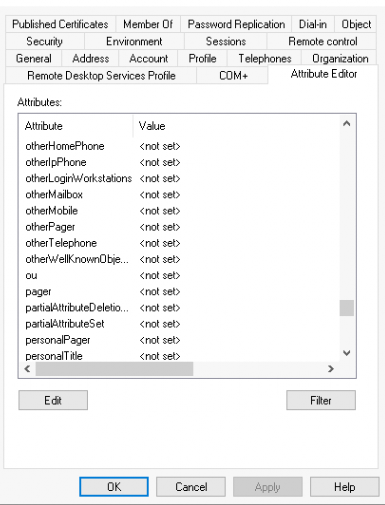
Go to your local AD and check user attributes: UPN, MAIL, and PROXY ADDRESS.
It must match the attributes of the existent objects on the cloud. You will find those attributes inside of user properties -> Attribute Editor
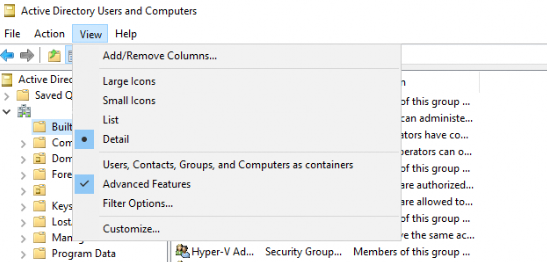
Tip: If you dont see “Attribute Editor” tab, you must enable “Advanced Features” in in view menu:
After completing synchronize the objects again and check if they are now linked.
Solution 2: Synchronizing Active Directory with Microsoft 365 through ImmutableID Adjustment
Even after meticulously matching all attributes between your Active Directory (AD) and Microsoft Entra ID, you might encounter stubborn synchronization issues. The reason behind these frustrating discrepancies can often remain a mystery. However, there’s a proven workaround that involves directly linking the AD object to its Microsoft 365 counterpart using a unique identifier.
ImmutableID
The ImmutableID attribute plays a critical role in maintaining the integrity of user objects across Active Directory and Microsoft 365 environments. By manually setting this attribute, we can force a match, resolving synchronization issues that defy other solutions.
Step 1: Retrieve the Object GUID
The journey to resolution begins within the familiar grounds of your Active Directory. Launch the PowerShell ISE and run the script below to transform the user GUID in ImutableID
# Solicita ao usuário para fornecer o SamAccountName de um usuário $UserSamAccount = Read-Host "Digite o SamAccountName do usuario" # Busca o usuário especificado no Active Directory e obtém a propriedade ObjectGUID $User = Get-ADUser $UserSamAccount -Properties ObjectGUID # Converte o ObjectGUID para ImmutableID (string base64) $ImmutableID = [system.convert]::ToBase64String(([GUID]($User.ObjectGUID)).ToByteArray()) # Exibe o ImmutableID do usuário Write-Host "ImmutableID do usuario $UserSamAccount é:" -ForegroundColor Yellow Write-Host $ImmutableID
With the GUID in hand, we can set it on users the Entra ID object.
Connect-MsolService Set-MsolUser -UserPrincipalName "[email protected]" -ImmutableId "ImutableID-From-AD"
By implementing this solution, you create a direct link between your on-premises AD object and its Microsoft 365 equivalent, effectively bypassing the mysterious synchronization barriers.